
-
“Bitcoin is giving banks a run for their money. Now the same technology threatens to eradicate social networks, stock markets, even national governments.”
-
“The “blockchain” — the engine on which Bitcoin is built — is a new kind of distributed consensus system that allows transactions, or other data, to be securely stored and verified without any centralized authority at all.”
– Jon Evans
-
“With blockchain technology, you could create a truly tamper-proof record system… records can go into the Blockchain in a way that I know if anybody tries to change it.”
– Peter Kirby
-
“You should be taking this technology as seriously as you should have been taking the development of the Internet in the early 1990’s.”
-
“Both the financial services and Bitcoin communities perked up last week when Citi, Nasdaq, Visa and other large financial institutions invested in Chain.com, a Bitcoin blockchain services provider.”
-
“Bitcoin is giving banks a run for their money. Now the same technology threatens to eradicate social networks, stock markets, even national governments.”
– Matthew Sparkes
-
“The “blockchain” — the engine on which Bitcoin is built — is a new kind of distributed consensus system that allows transactions, or other data, to be securely stored and verified without any centralized authority at all.”
– Jon Evans
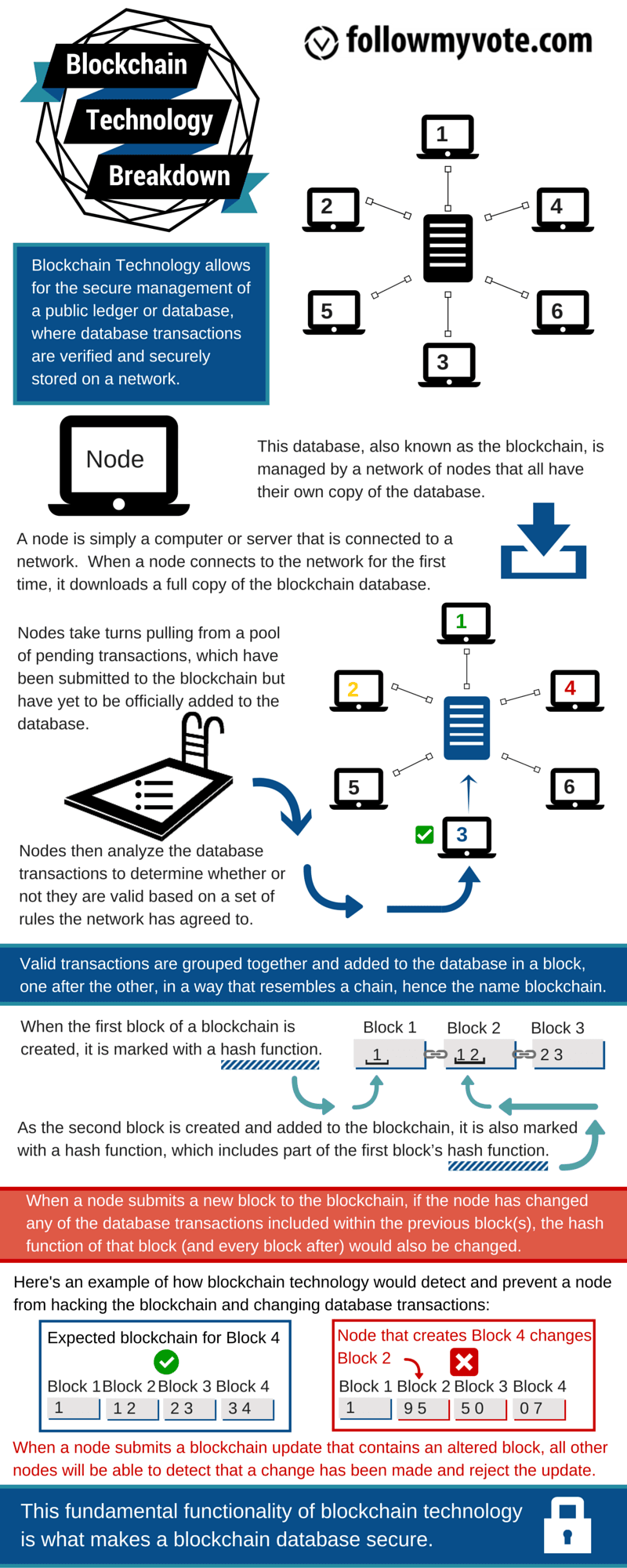
A blockchain is an audit trail for a database which is managed by a network of computers where no single computer is responsible for storing or maintaining the database, and any computer may enter or leave this network at any time without jeopardizing the integrity or availability of the database. Any computer can rebuild the database from scratch by downloading the blockchain and processing the audit trail.
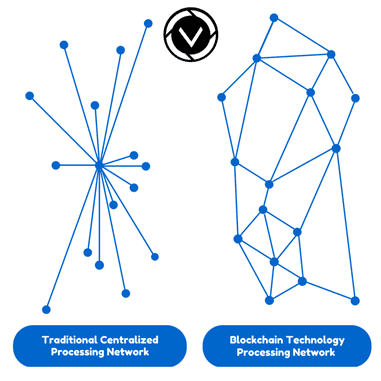
Traditional databases are maintained by a single organization, and that organization has complete control of the database, including the ability to tamper with the stored data, to censor otherwise valid changes to the data, or to add data fraudulently. For most use cases, this is not a problem since the organization which maintains the database does so for its own benefit, and therefore has no motive to falsify the database’s contents; however, there are other use cases, such as a financial network, where the data being stored is too sensitive and the motive to manipulate it is too enticing to allow any single organization to have total control over the database. Even if it could be guaranteed that the responsible organization would never enact a fraudulent change to the database (an assumption which, for many people, is already too much to ask), there is still the possibility that a hacker could break in and manipulate the database to their own ends.
The most obvious way to ensure that no single entity can manipulate the database is to make the database public, and allow anyone to store a redundant copy of the database. In this way, everyone can be assured that their copy of the database is intact, simply by comparing it with everyone else’s. This is sufficient as long as the database is static; however, if changes must be made to the database after it has been distributed, a problem of consensus arises: which of the entities keeping a copy of the database decides which changes are allowed and what order those changes occurred in? If any of the entities can make changes at any time, the redundant copies of the database will quickly get out of sync, and there will be no consensus as to which copy is correct. If all of the entities agree on a certain one who makes changes first, and the others all copy from it, then that one has the power to censor changes it doesn’t like. Furthermore, if that one entity disappears, the database is stuck until all of the others can organize to choose a replacement. All of the entities may agree to take turns making changes and all the others copy changes from the one whose turn it is, but this opens the question of who decides who gets a turn when.
How Blockchain Technology Works
Blockchain technology solves these problems by creating a network of computers (called nodes) which each store a copy of the database, and a set of rules (called the consensus protocol) which define the order in which nodes may take turns adding new changes to the database. In this way, all of the nodes agree as to the state of the database at any time, and no one node has the power to falsify the data or to censor changes. The blockchain further requires that an audit trail of all changes to the database is preserved, which allows anyone to audit that the database is correct at any time. This audit trail is composed to the individual changes to the database, which are called transactions. A group of transactions which were all added by a single node on its turn is called a block. Each block contains a reference to the block which preceded it, which establishes an ordering of the blocks. This is the origin of the term “blockchain”: it is a chain of blocks, each one containing a link to the previous block and a list of new transactions since that previous block. When a new node joins the network, it starts with an empty database, and downloads all of the blocks, applying the transactions within them to the database, to fast-forward this database to the same state as all the other nodes have. In essence, a blockchain establishes the order in which transactions were applied to the database so that anyone can verify that the database is accurate by rebuilding it from scratch and verifying that at no point was any improper change made.
The most obvious example of blockchain technology in use today is Bitcoin. Bitcoin is a digital currency system which uses a blockchain to keep track of ownership of the currency. Whenever someone wishes to spend their bitcoins, they create a transaction which states that they are sending a certain number of their bitcoins to someone else. Then they digitally sign this transaction to authorize it, and broadcast it to all of the nodes in the Bitcoin network. When the next node creates a block, it will check that the new transaction is valid, and include it in the new block, which is then propagated to all other nodes in the network, which adjust their databases to deduct the transferred bitcoins from the sender and credit them to the recipient.
Blockchain Consensus Protocols
As mentioned above, blockchains are governed by a set of rules called the consensus protocol. These rules define which changes are allowed to be made to the database, who may make them, when they can be made, etc. One of the most important aspects of the consensus protocol are the rules governing how and when blocks are added to the chain. This is important because in order for blockchains to be useful, they must establish an unchangeable timeline of events, which must be agreed upon by all nodes, so that all nodes can agree on the current state of the database. Moreover, this timeline cannot be subject to censorship, thus no single node may be entrusted with control over what enters it when. There are currently two main types of consensus protocol: Proof of Work (PoW) and Proof of Stake (PoS).
Proof of Work is the original consensus protocol, and is currently used by Bitcoin, Ethereum (as of January, 2016), and many other blockchains. Proof of Work is based on puzzles which are difficult to solve, but once solved, it’s easy to verify that the solution is correct. This is analogous to a jigsaw puzzle: hours of effort are required to put the puzzle together, but it takes only a momentary glance to see that one has been assembled correctly. In Proof of Work consensus, the effort required to solve a puzzle is called Work, and a solution is called a Proof of Work. In other words, the fact that I know the solution to the puzzle proves that someone did the work to find that solution. The solution is proof that someone did work. Blockchains which use Proof of Work consensus require such proof for each new block to be added to the chain, thus requiring Work to be done to create new blocks. This Work is frequently referred to as ‘mining.’ Proof of Work consensus protocols state that the chain containing the most blocks is the correct chain because it contains the most work. Blockchains which use Proof of Work are regarded as secure timelines because if one node attempted to rewrite history by changing an old block, its change would invalidate the work on the block it changed and all blocks after it by making the Proofs incorrect. In order to convince other nodes that the modified chain is the correct chain, that node would have to redo all of the work in all of the blocks after his change to make new, valid Proofs, and because all other nodes are still making new blocks with new Proofs and adding them to the original chain, the one node would have to redo all of the old work faster than all other nodes combined in order to catch up and surpass the original chain. This is known as a 51% attack, so named because the one node would have to have at least 51% of the computational power (ability to do Work and find Proofs) of all nodes combined. If this attack were successfully carried out, the attacking node would be able to censor transactions from the blockchain, change the order in which transactions occurred, or change transactions that node made (but the node would be unable to change any other node’s transactions).
Proof of Stake is a newer consensus protocol which was developed to address some perceived weaknesses in Proof of Work and is currently utilized by Peercoin, BitShares, and several other blockchains. Some of the advantages of Proof of Stake are that no Work is required, thus it requires less energy; the 51% attack is theoretically more expensive; and PoS may encourage a more decentralized network of nodes than PoW. Proof of Stake consensus protocols have more varied rules governing which nodes may create new blocks when than Proof of Work protocols, but in general all PoS protocols specify that block production is controlled by Stake in the blockchain rather than computational power. Stake in the blockchain is balances in the currency the blockchain tracks, thus the greater the balance a node owns, the more say that node has in block production. Proponents of Proof of Stake consensus protocols argue that owners of large amounts of stake will wish to protect their investment and thus will take action to ensure block production continues smoothly and securely. Attacks on the network will damage trust in the network, thereby devaluing the stake. A 51% attack would require the attacker to buy 51% of the stake in the network, which would be extremely expensive since the more stake the attacker buys, the higher the price will rise, and using that stake to attack the network will result in a complete loss since the value of the stake would be destroyed by the attack. This is as compared with a 51% attack on a Proof of Work blockchain, which requires only computing power which typically becomes cheaper when purchased in bulk, and can be repurposed or sold when the attack is complete. It is further supposed that, whereas Proof of Work consensus incentivizes greater centralization because computing power is cheaper with centralized cooling and power, no such incentive exists with Proof of Stake since a typical smartphone has more than sufficient computational power to produce blocks for a PoS blockchain.
Blockchain Technology and Online Voting
Another application for blockchain technology is voting. By casting votes as transactions, we can create a blockchain which keeps track of the tallies of the votes. This way, everyone can agree on the final count because they can count the votes themselves, and because of the blockchain audit trail, they can verify that no votes were changed or removed, and no illegitimate votes were added.
Check out our blockchain technology info-graphic!
Are You a Blockchain Developer?
Original article and pictures take followmyvote.com site
Комментариев нет:
Отправить комментарий